Upcoming Applications, Challenges, Need of Security And Future Scopes of Internet-of-Things (IoT)
Constructively, ‘availability' is an integral component that influences the overall performance of IoT [2]. As the net continues to evolve, it has emerged as extra than a easy community of computers, however rather a community of a number devices, whilst IoT serves as a neighbourhood of pretty a wide variety of “connected” gadgets community of networks. Nowadays, devices like smartphones, vehicles, industrial systems, cameras, toys, buildings, home appliances, industrial structures, and countless others can all share information over the Internet.
Regardless of their sizes and functions, these devices can accomplish clever reorganizations, tracing, positioning, control, real-time monitoring, and device control. Also, there are some different phrases associated to IoT such as IoE (Internet of Everything), WoT (Web of Things), CoT (Cloud of Things), M2M (Machine to Machine), etc. Currently, an estimated range of totally 0.6% of devices that can be section of IoT has been linked so some distance. While industrial success continues to materialize, the IoT always offers a absolutely limitless furnish of opportunities, now no longer in reality in businesses however moreover in research.
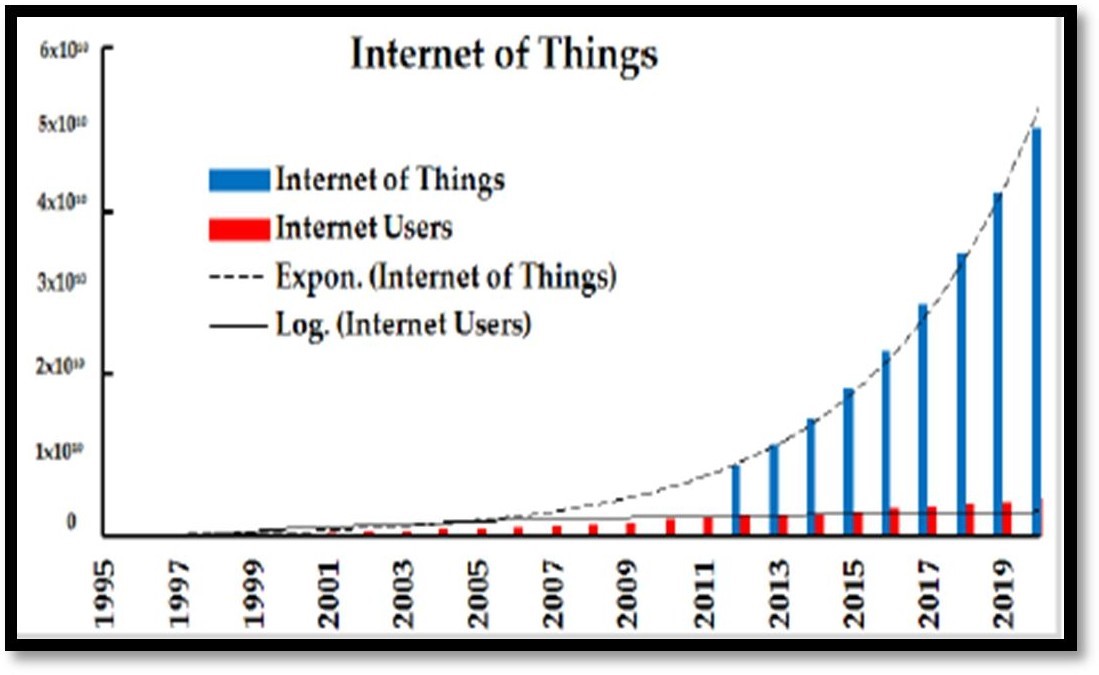
Thus, the major goal of IoT is to make it viable for objects to be related with different objects, individuals, at any time or somewhere the usage of any network, path, or service. IoT is step by step being considered as the subsequent section in the Internet evolution. IoT will make it feasible for normal units to be linked to the net in order to acquire endless disparate goals. According to International Telecommunication Union (ITU) [3] standards, IoT is “a worldwide infrastructure for the facts society that allows superior offerings with the resource of interconnecting (physical and virtual) things in particular based totally on present day and evolving interoperable archives and verbal alternate technologies”.
I. UPCOMING APPLICATIONS OF IOT
In terms of connectivity, ITU-T realised IoT as a network with anyplace and whenever connectivity for all of us or anything. In order to discover and discuss technology-based issues, this paper offers a classification of IoT enabling applied sciences in accordance to their functionalities.
1. Iot in Smart Urban Communities
As indicated with the aid of capability of [6], the IoT assumes a critical job in enhancing the smartness of city communities and upgrading common foundation.
Some IoT utility territories in making wise metropolis areas incorporate; canny transportation frameworks [7], sensible structure, visitors clog [7,8] squander administration [9], clever lighting, clever shopping, and metropolis maps. This might also moreover contain pretty a wide variety of functionalities. Insightful interstates can grant cautioning messages and sizeable data. Such features will provide indispensable leaps ahead as some distance as putting aside money and vitality.
2. Iot in Healthcare
Most medicinal offerings frameworks in countless international locations are wasteful, slow, and always inclined to blunder. Extra innovation that can encourage unique obligations like file sharing to several humans and areas, document retaining, and administering drugs would go a lengthy way in altering the social insurance plan part [10]. A super deal of benefits that IoT software program affords in the social insurance plan part is usually categorized into the following of patients, staff, and items, recognizing, simply as confirming, people, and the programmed assembling of data and detecting.
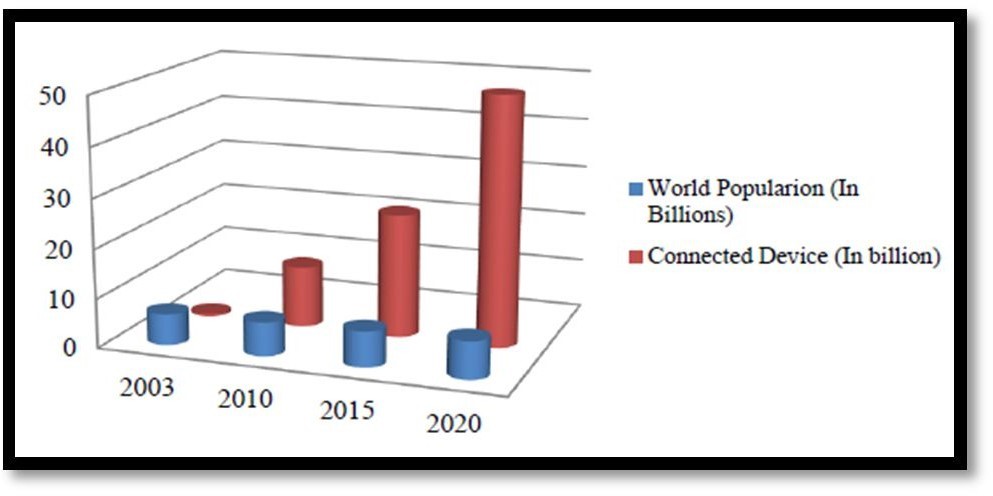
3. Iot in Smart Living
Right now, can be utilized in far-off manipulating devices whereby one can remotely flip apparatuses on and off for this reason forestalling mishaps certainly as sparing vitality [11]. Other smart home machines include fridges equipped with LCD (Fluid Gem Show) screens, empowering one to comprehend what is handy inside, what has overstayed and is nearly lapsing sincerely as what wishes to be restocked.
These facts can likewise be associated to a smartphone utility empowering one to get to it when outside in the house and alongside these traces buy what is required.
4. IoT and Sensors
The data produced by using most sensors are no longer used efficiently. To aid the technological know-how, evolve, 62% of surveyed producers take delivery of as authentic that its overall performance can be accelerated via advancing analytics features. More education on analytics equipment used to be as soon as additionally concept to be one way by using skill of 45% people. More mobility, computing electricity, and attainable to preserve records had been moreover some elements mentioned with the aid of the manufacturers.
5. IoT and Mobile Data
The effectiveness of the era of facts from IoT sensors is poor. The data is typically collected thru smartphones which have an quintessential position in IoT.
The person interfaces for IoT purposes are furnished with the useful resource of smartphones. Consider the instance of domestic automation: in the case of vital home-monitoring and protection applications, is it definitely really worth counting upon a smartphone.
- What will happen?
- When the person’s smartphone goes into plane mode throughout his travel?
- Does the electrical energy shut down or, his home protection gets interrupted?
- What if the sensors stopped working abruptly?
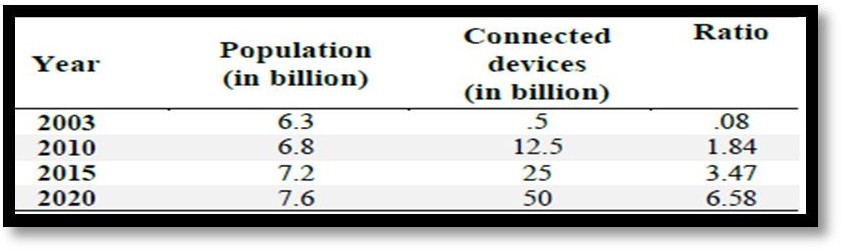
1. IoT and Volume of Data
Most medicinal offerings frameworks in countless international locations are wasteful, slow, and always inclined to blunder. Extra innovation that can encourage unique obligations like file sharing to several humans and areas, document retaining, and administering drugs would go a lengthy way in altering the social insurance plan part [10]. A super deal of benefits that IoT software program affords in the social insurance plan part is usually categorized into the following of patients, staff, and items, recognizing, simply as confirming, people, and the programmed assembling of data and detecting.
2. IoT and Datacentres
There is constantly the constant argument that: Data in datacentres manages all the strategies in IoT. It is a univocal truth that the datacentre is definitely a critical element of the IoT. We need to additionally focally factor on the reliability of the neighbourhood which is used to run the IoT applications. High-speed Internet is equally essential as its overall performance the functionalities like the dependable transmission of data, rapid shipping of sensor data, fetching small print from sensors to a cloud, and vice versa [12].
II. CHALLENGES IN IOT
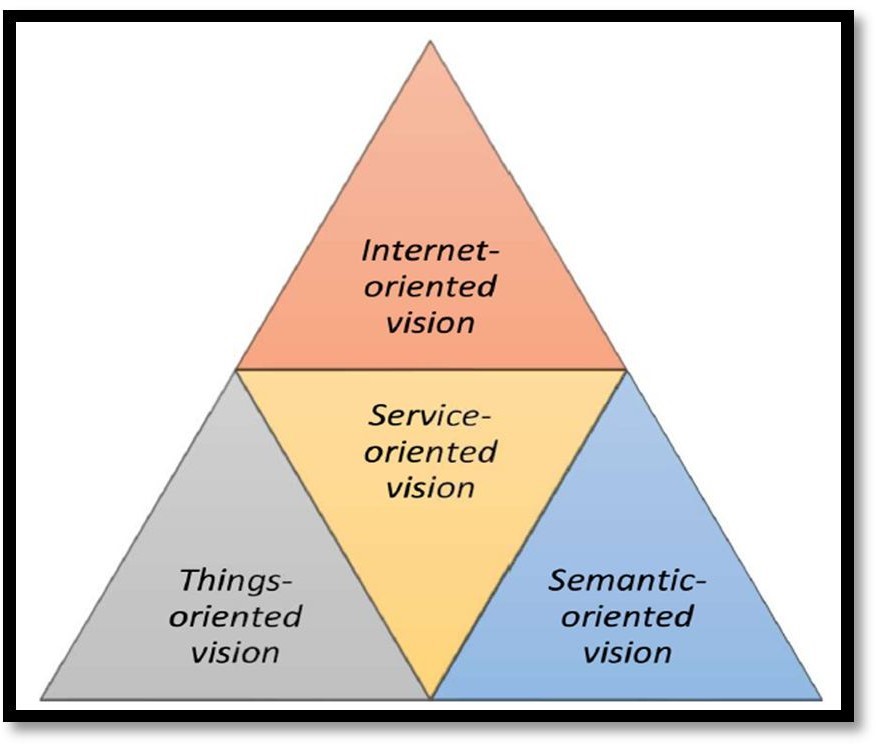
1. Efficient Data Handling Challenges
As a long way as any paradigm cares, one of its important elements is data. This fact should additionally be modified data, generated data, saved data, and statistics inside the transit. inside the case of IoT, information series varieties a serious challenge. Many researchers are now then discussing the significance of information mining inside the discipline of IoT. [13], one of the most essential issues inside the subject and recognition of IoT is “Data change amongst large-scale heterogeneous community elements”. More intensive statistics perception is required to fight the uncertainties like non-uniformity, inconsistency, inaccuracy, and discontinuities.
2. Societal Challenges
After discussing the technological challenges and their inclusive literature survey, at now, this work quickly discusses any other challenge, i.e., societal mission [14]. As we've got already elaborated a variety of functions of IoT, such as several societal functions in Section 2, pointless to mention, that the challenges will comply with up with an equal enormity. The main societal task is brain breach. In different words, though the planet is shifting with a excessive rapidity toward IoT, nevertheless the planet is missing the professional crowd to put into effect IoT successfully. Mohanty et al. [3] analyzed the depend of analysts to assessment the large- scale facts for environment friendly use. The authors cautioned the utilization of large
Data analytics and algorithm-based approached to confront things. Another essential societal venture is disapproval of the novel paradigm via the masses. Using IoT for quite a number functions is one of the high leads of IoT, however its growth stays hampered due to the fact it is nevertheless no longer applicable via people. Asplund and Nadim-Tehrani [16], carried out a survey that supported a gaggle of inquiries to a crew of actors. Authors recorded the standard understanding and hazard grasp of loads on IoT. the explanations at the back of dissatisfaction of end-users contain privateness issues, financial issues, or perhaps soreness toward the distinction of today's technology. Conclusively, to set up self-belief amongst the pinnacle users, practitioners want to work very challenging and long. Although “efficient facts handling” may also be a technological challenge, nevertheless an equal problem arrives right here at some point of a special presentation.
3. Environmental Challenges
The effectiveness of science is immediately linked to the enormity of associated challenges. As a way as IoT cares, it is one of the fantastic paradigms that make the user’s existence less difficult to measure. After the web, cloud computing, cellular computing, and similar paradigms, whose influences have been up-to-the information world only, IoT has it’s had an effect on the bodily world also, truly comprising the records world in it [11]. due to the fact the Internet can make a statistics world a whole lot less difficult to work-in, in a similar fashion IoT makes the bodily world surroundings extra best to stay in.
The essential environmental mission with IoT is electricity consumption. As computing will become an inevitable phase of every and each and every element of human life, electricity consumption turns into an inescapable problem too. Therefore, practitioners want to work on low electricity consumption through the clever gadgets getting used in IoT implementation. Another mission into account is financial system and price. Billions of IoT gadgets are getting used and can be planted in close to future to accomplish success.[6], mentioned the mission of cost-benefit trade-off inside the context of large investments in IoT and not sure returns. However, up to now, no important answer has been generated to attenuate the price of IoT devices. the cost of an IoT machine ought to be extraordinarily low; therefore, it is as an alternative vital to provide considerate consideration to the monetary
4. Standardization
Diversities in utilized sciences and requirements are diagnosed as one of the predominant challenges in the enhancement of IoT features [5]. Standardization of IoT structure and verbal change applied sciences is regarded as a backbone for IoT enhancement in the future [8]. These information endorse that open necessities are one of the key elements for the profitable deployment of IoT. This type of requirement is an vital facilitator for innovation due to the truth of their availability to the public.
They are being developed, approved, and maintained through skill of a collaborative consensus-based decision-making approach to furnish greater interoperability for constructions the utilization of distinctive technologies.
Also, by means of way of the use of open requirements, there is a great deal much less hazard of being restrained to a particular provider or science which is a very indispensable element for IoT development. The fundamental standardization our bodies such as ITU, ETSI, IETF, IEEE, W3C, OneM2M, OASIS, NIST, etc. are concerned in the effort to make a framework for IoT standards. The scopes of standardization things to do are more than a few in order to furnish open necessities and architectures, seamless connectivity, interoperability, etc. All these open troubles and challenges favour to be viewed in the future to allow seamless connectivity as well as the integration and interoperability amongst a quantity of IoT enabling technologies.
5. Intelligent Analysis & Actions
The closing step in the implementation of IoT is the revelation about the data for analysis. The evaluation approach is specifically primarily based on cognitive applied sciences and models. There are positive parameters that purpose wise movements to be protected in IoT, some of them being lesser computing device cost, higher machine functionality, the laptop computer "influencing" human actions by way of behavioural-science rationale, deep getting to comprehend tools, machines’ actions in unusual scenarios, facts protection and privateness and machine interoperability.
6. Connectivity
The hugest project of the future of IoT would be to join several devices, this verbal exchange will end up resisting the presently modern shape and, the applied sciences associated to it. But now, present a centralized server/client structure is being utilized to authenticate, authorize and join quite a few terminals in a network.
7. Compatibility and Longevity
IoT is creating in a large manner. It is incorporating many applied sciences and will quickly strengthen into a convention. This will pose serious challenges and will demand the putting up of extra software program and hardware in order to establish conversation amongst the devices.
III. NEED OF SECURITY IN IOT

IoT has taken place to purpose the most vital safety issues that have grabbed the activity of a range of public and non-public area firms of the world. Adding such a giant vary of new hubs to the structures and the internet will supply attackers with a large platform to invade the system, normally as many journeys the sick penalties of protection holes. Indications suggested that the malware captured a countless range of IoT units that are being used in integral purposes like smart-home devices and closed-circuit cameras and deployed them closer to their private servers. A in a similar way imperative cross in protection will enlarge from the way IoT turns out to be involved in our lives. Some study about proves that cameras related to the web will make a contribution 30% to protection concerns. Others are being 15% on house doors, 12% on cars, 10% on TVs, 6% due to iron, 6% on heating systems, 6% on smoke systems, 5% and 5% on an oven and lightening each.
1. Issues with IoT security
A safety vulnerability is a weak spot which can be exploited to compromise the integrity or availability of your IoT application. IoT units with the aid of capacity of nature, are vulnerable. IoT fleets consist of devices that have various capabilities, are long-lived, and are geographically distributed. These characteristics, coupled with the creating volume of devices, elevate questions about how to tackle protection dangers posed with the resource of IoT devices. To in a similar fashion make bigger safety risks, many units have a low-level of compute, memory, and storage capabilities, which limits possibilities for enforcing protection on devices. Even if you have utilized excellent practices for security, new assault vectors are continuously emerging. To find out and mitigate vulnerabilities, organizations ought to continuously audit machine settings and health.
2. Security Isn’t a Market Priority?
The actuality is that IoT units are designed with the intention of getting to market earlier than the opposition does. This ability that corners may also moreover be cut. Since safety isn’t seen a promoting point, it’s commonly what receives the quick shrift.
3. IoT privacy and Security
Security and privateness are the predominant concerns while designing and growing IoT devices and addressing these issues ought to be an excessive priority. New science regularly has scope for abuse, and it’s smarter to resolve the trouble previously than it influences privations and security, innovation or financial development. It is a duty of Manufacturers, requirements groups and policy-makers to address all the potential threats to the product. As a segment of community layer security, producers need to suppose about the implementation of new security protocols that will be critical to assurance end-to-end transmission of refined data.
4. Secure Route Establishment
One of the key challenges is to set up tightly closed routing protocol for facts transmission in IoT. Such a protocol has to be in a position to securely set up a route and warranty impervious route amongst speaker nodes, computations carried out for the cause of routing facts must be lightweight in order to be safely served through the low-powered IoT networks.
5. Isolation of Malicious Nodes
Another project is to shortly and robustly recognise malicious nodes and format techniques to isolate them from the IoT networks protocol have to be capable to isolate misbehaving of the nodes in the neighbourhood so that disruption in the routing machine is minimized or eradicated altogether. Current routing protocols for IoT are insecure as most IoT networks are self-organizing and typically function beside any human involvement. Hence, malicious nodes can be brought in the IoT community with relative ease, so there is a prefer to design a protocol that has strategies and techniques to block malicious nodes from becoming a member of the neighbourhood or find out them as quickly as they begin malicious activities.
6. Self-Stabilization of the Security Protocol
The Protocol desires to self-stabilize which would potential it must be successful to get better routinely from any kind of trouble inside a positive time barring human involvement.
7. Preservation of Location Privacy
The Location privateness must be maintained for the IoT devices in the IoT network. Hence, for a impenetrable routing protocol, it ought to be capable to preserve neighbourhood privacy.
8. IoT and confined vendors
Open structures have generally been a tested way for builders and outlets to assemble modern hardware with restrained spending plans and property [14]. The behaviour of IoT features has heterogeneous nature. Hence it requires a massive vary of software program and hardware. To manufactures all these IoT components, there want to be a full quantity of carriers on hand in the market.
9. Profiling & Tracking
Association of an identification with a special man or woman ought to be a chance as this may additionally purpose identification and chase. Hence, one amongst the key challenges is to compel such endeavour in IoT and take some preventive measures.
10. Localization & Tracking
The Localization is some other hazard as structures try to verify and record a person’s area via time and area. one of all the key challenges of security alternatives for IoT is to trend the protocols for interactions with IoT that daunts such activity identification files related with a specific person to infer pastimes by way of way of correlation between desire profiles and, the records is relatively frequent in e-commerce applications. the massive project lies in reconciliation pastimes of organizations for identification and statistics evaluation with user’s privations needs.
11. Secure Data
Yet each different protection is to make positive that facts is transmitted in a very tightly closed manner via the popular public medium besides concealing records to all of us and thereby provide up unauthorized assortment of facts involving things and different people.
12. Hackable Cardiac Devices
IoT is propelling massive advances in healthcare. Some of these advances, such as the radio-controlled implantable cardiac gadgets developed by way of way of St. Jude Medical, are more relatively invasive. These devices have been developed with a vulnerability that allows attackers to get entry to and reprogram them. In theory, this may also choose to allow an attacker to administer inappropriate stages of pacing, doubtlessly inflicting victims to die.
IV. FUTURE SCOPE
The uncertainty and employer risk are usually current in any new technology. In the case of IoT, it is observed that many of the risks are bodily now not current specially they are distorted or misstated.
Potential functions of the net of Things are no longer solely several however additionally tremendously a range of as they permeate into without a doubt all elements of the way of lifestyles of humans, institutions, and society. constant with [4], the features of IoT cowl giant areas which consist of manufacturing or the health sector, smart cities, security, and emergencies amongst many others. While it will take time to increase the IoT imaginative and prescient fully, the setting up blocks to begin the technique are geared up to be used.
The fundamental requirements such as - hardware and software program property is both handy in a much less volume or some of them are beneath development; it is moreover a truth that: the safety and confidentiality problems of IoT devices are no longer genuine addressed over the preceding decade.
Over the subsequent few years, IoT is anticipated to make over $19 trillion [5]. However, the hassle related with this: these ‘things' have myths surrounding them, some of which are impacting how corporations decorate the apps to information them.
V. CONCLUSION
The paper goes via more than a few aspects of what the future of IoT looks like. Though chains of myths will usually preserve the future with uncertainty, the situation can be considered to grow to be better shortly if we work on disposing of them. While using facts accumulated from sensors wisely, the dependency of IoT on cellular networks, the importance of the records generated from different devices, importance of networks alongside datacentres, want of a secured carrier infrastructure with far off manipulating options, the evolution of interoperability standards, heterogeneity and openness are some of the problems that need to be addressed, safety and privations of information will play a major role in how the picture of IoT will appear like in the coming decades.
Parallel to it also comes to the challenges faced with the aid of this technology that poses a risk to its success. Every element including technology, business, society, and regulation face up to the success charge of IoT. Acceptance of technology by people is additionally critical and be taken into consideration at some point of its development as people who are no longer fond of using gadgets, smart gadgets and do no longer experience cozy dealing with technology will have a challenging time working with the complexity performance IOT will engage them with. It's excessive time to deal with the factors that might extensively carry down the mighty future of IoT.
Author

Aditya Raj Singh
- Aditya Raj Singh, Student of Shri Ram College of Commerce, (SRCC)






