Breification 17 : What is a Botnet attack?
What is a Botnet?
A botnet is a network of computers running bots under the control of a bot herder. Botnets are networks of hijacked computer devices used to carry out various scams and cyberattacks. A bot is also called a zombie, and a botnet is referred to as a zombie army.
The term “botnet” is formed from the words “robot” and “network.” The Assembly of a botnet is usually the infiltration stage of a multi-layer scheme. Bots are software applications that run automated scripts over a network, while a bot herder is a person controlling and maintaining the botnet.
What is Botnet Controllable?
Candidates for botnet recruitment can be any device that can access an internet connection.
Many devices we use today have some form of computer within them — even ones you might not consider. Nearly any computer-based internet device is vulnerable to a botnet meaning the threat is constantly growing. To protect yourself, take note of some common devices that are hijacked into botnets:
- Traditional computers like desktops and laptops that run on Windows OS or macOS have long been popular targets for botnet construction.
- Mobile devices have become another target as more people continue to use them. Smartphones and tablets have notably been included in botnet attacks of the past.
- Internet infrastructure hardware used to enable, and support internet connections may also be co-opted into botnets. Network routers and web servers are known to be targets.
Internet of Things (IoT) devices include any connected devices that share data with each other via the internet. Alongside computers and mobile devices, examples might include:

- Smart home devices (thermometers, security cameras, televisions, speakers, etc.)
- In-vehicle infotainment (IVI)
- Wearable devices (smartwatches, fitness trackers, etc.)
Collectively, all these devices can be corrupted to create massive botnets. The technology market has become oversaturated with low-cost, low-security devices, leaving you particularly vulnerable as a user. Without anti-virus malware, bot herders can infect your devices unnoticed. Centralized models are driven by one bot herder server. A variation on this model may insert additional servers tasked as sub-herders, or “proxies.” However, all commands trickle down from the bot herder in both centralized and proxy-based hierarchies. Either structure leaves the bot herder open to being discovered, which makes these dated methods less than ideal.
Decentralized models embed the instruction responsibilities across all the zombie computers. As long as the bot herder can contact any one of the zombie computers, they can spread the commands to the others. The peer-to-peer structure further obscures the identity of the bot herder party. With clear advantages over older centralized models, P2P is more common today.
A botnet is similar to those of other cybercrimes. In many cases, these attackers either want to steal something valuable or cause trouble for others. In some cases, cybercriminals will establish and sell access to a large network of zombie machines. The buyers are usually other cybercriminals that pay either on a rental basis or as an outright sale. For example, spammers may rent or buy a network to operate a large-scale spam campaign.
Despite the many potential benefits for a hacker, some people create botnets just because they can. Regardless of motive, botnets end up being used for all types of attacks both on the botnet-controlled users and other people.
Types of Botnet Attacks
While botnets can be an attack in themselves, they are an ideal tool to execute secondary scams and cybercrimes on a massive scale. Common botnet schemes include some of the following:
1. Distributed Denial-of-Service (DDoS)
It is an attack based on overloading a server with web traffic to crash it. Zombie computers are tasked with swarming websites and other online services, resulting in them being taken down for some time.
2. Phishing
schemes imitate trusted people and organizations for tricking them out of their valuable information. Typically, this involves a large-scale spam campaign meant to steal user account information like banking logins or email credentials.
3. Brute force
Brute force attacks run programs designed to breach web accounts by force. Dictionary attacks and credential stuffing are used to exploit weak user passwords and access their data.
Famous Botnet Attacks
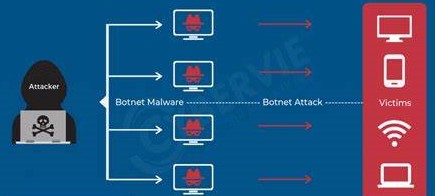
Now that you have understood how a botnet works, you can imagine how dangerous it can be. The networks of enslaved devices are behind various dangerous cyber attacks. You will now look at a few sophisticated botnets.
· Mirai
Mirai is one of the famous botnets associated with IoT devices. First found in 2016, it primarily targets online consumer devices and has been used in some of the most disruptive DDoS attacks.
· Mariposa
Emerged in 2009, the Mariposa botnet committed online scams and launch DDoS assaults. It was also stealing personal account credentials from victims so that its operators could sell them on the Dark Web.
· Zeus
This financial Trojan accounted for 90% of all global online bank fraud instances at their peak. Emerging in July 2007, it was used to steal data from the United States Department of Transportation.
· Storm
First identified in 200, Storm was one of the first P2P botnets with a massive network ranging from 250,000 to 1 million infected devices. The Storm handled attacks from DDoS to identify theft.
· 3ve
First discovered in 2016, 3ve was a different type of Botnet that did not steal data or money and instead generated fake clicks on online advertisements hosted by fake websites.
How Do Hackers Control a Botnet?
Issuing commands is a vital part of controlling a botnet. However, anonymity is just as important to the attacker. As such, botnets are operated via remote programming. Command-and-control (C&C) is the server source of all botnet instruction and leadership. This is the bot herder's main server, and each of the zombie computers gets commands from it.
Each botnet can be led by commands either directly or indirectly in the following models:
- Centralized client-server models
- Decentralized peer-to-peer (P2P) models
What Are Botnets Used For?

Botnet creators always have something to gain, whether for money or personal satisfaction.
Financial theft — by extorting or directly stealing money
Information theft — for access to sensitive or confidential accounts
Sabotage of services — by taking services and websites offline, etc.
Cryptocurrency scams — using users’ processing power to mine for cryptocurrency
Selling access to other criminals — to permit further scams on unsuspecting users
Basic stages of building a botnet can be simplified into a few steps:
Prep and Expose — hacker exploits a vulnerability to expose users to malware.
Infect — user devices are infected with malware that can take control of their device.
Activate — hackers mobilize infected devices to carry out attacks.
You’re probably still are asking, “what does a botnet do?” Once infected, a zombie computer allows access to admin-level operations, such as:
- Reading and writing system data
- Gathering the user’s personal data
- Sending files and other data
- Monitoring the user’s activities
- Searching for vulnerabilities in other devices
- Installing and running any applications
How Does a Botnet Work?
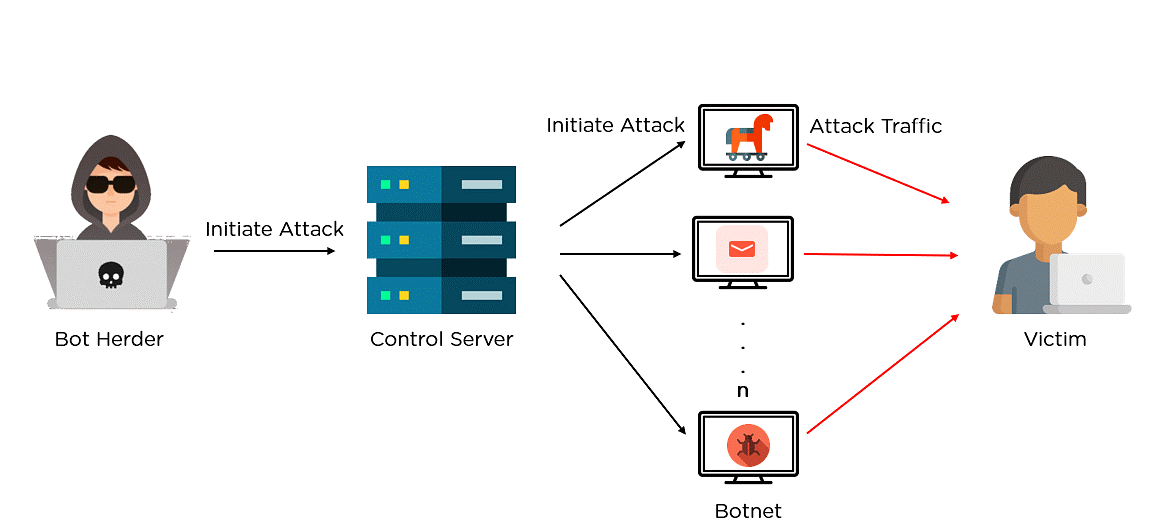
Now that you have a good understanding of what is a botnet, it’s time to dive deeper into learning how a botnet works. Below are the steps that are carried out to initiate a botnet attack:
1. Prepping the Botnet Army
The first step in creating a botnet is to infect as many connected devices as possible, to ensure that there are enough bots to carry out the attack. It uses the computing power of the infected devices for tasks that remain hidden to the device owners. However, the fraction of bandwidth taken from a single machine isn't sufficient, and hence the Botnet combines millions of devices to carry out large-scale attacks. This way, it creates bots either by exploiting security gaps in software or websites or phishing emails. They often deploy botnets through a trojan horse virus.
2. Establishing the connection
Once it hacks the device, as per the previous step, it infects it with a specific malware that connects the device back to the central botnet server. This way, it connects all the devices within the botnet network, and they are ready to execute the attack. A bot herder uses command programming to drive the bot's actions.
3. Launching the attack
Once infected, a bot allows access to admin-level operations like gathering and stealing user data, reading and writing system data, monitoring user activities, performing DDoS attacks, sending spam, launching brute force attacks, crypto mining, and so on.
Botnet Architecture
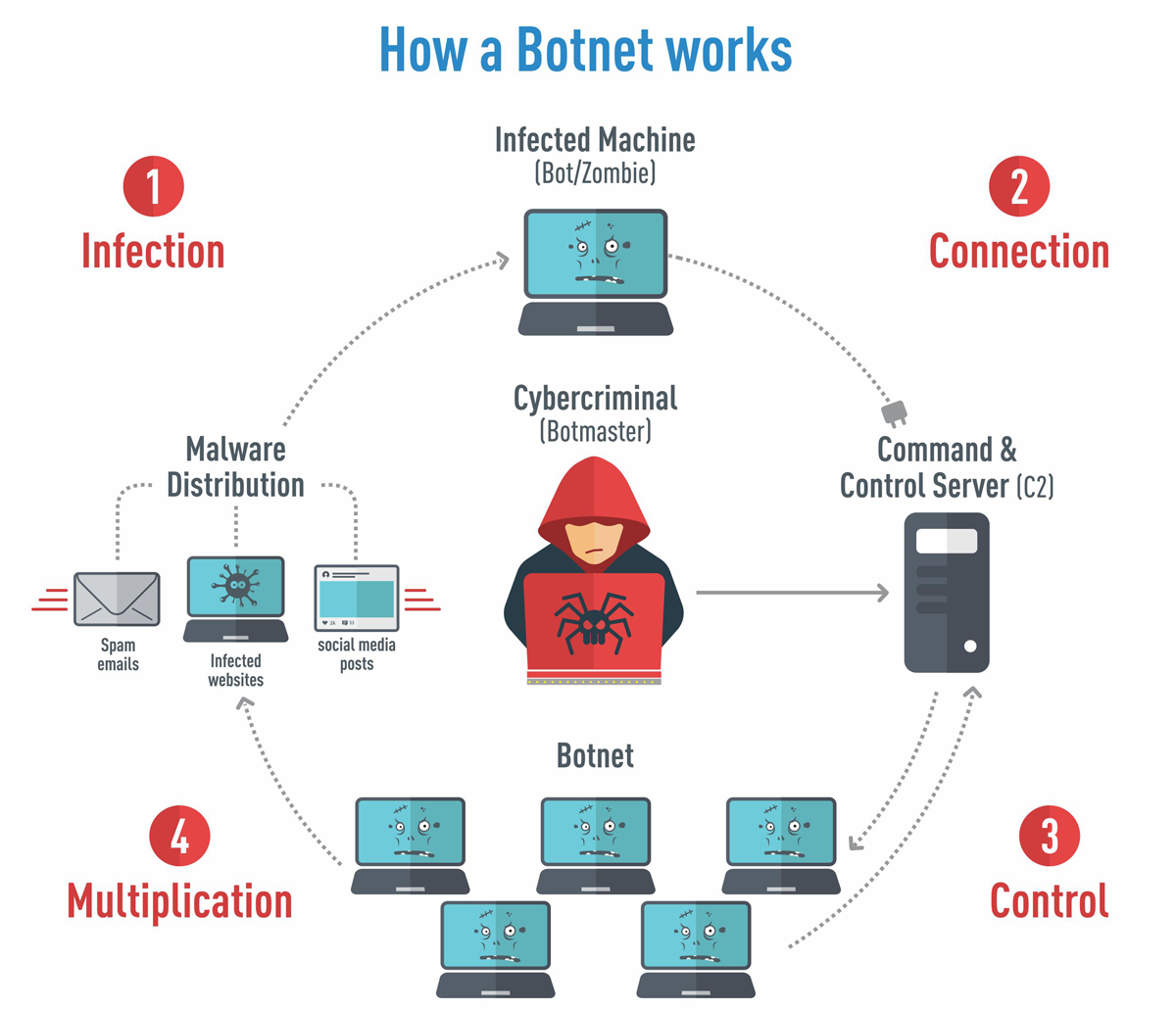
A botnet architecture has developed over a while for improved working and slimmer chances of getting traced. As seen previously, once it infects the desired number of devices, the botmaster (bot herder) takes control of the bots using two different approaches.
· Client-Server Model
The client-server model is a traditional model that operates with the help of a command and control (C&C) server and communication protocols like IRC. For example, IRC or Internet Relay Chat sends automated commands to the infected bot devices.
Before engaging in a cyberattack, it frequently programs the bots to remain dormant and await commands from the C&C server. When the bot herder issues a command to the server, it is then relayed to the clients. Following this, the clients run the commands and report the findings to the bot herder.
· The P2P Botnet
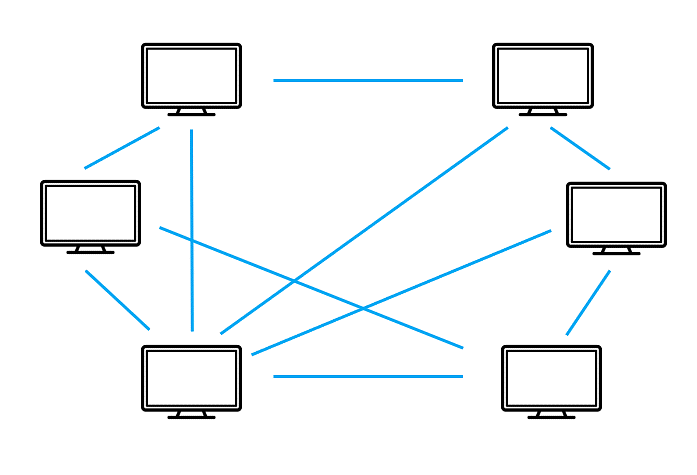 Instead of using C&C servers, we have the P2P approach. Here, controlling infected bots involves a peer-to-peer network that relies on a decentralized approach. As seen in the above image, bots are topologically interconnected and act as both C&C servers and clients. Today, hackers adopt this approach to avoid detection and single-point failure.
Instead of using C&C servers, we have the P2P approach. Here, controlling infected bots involves a peer-to-peer network that relies on a decentralized approach. As seen in the above image, bots are topologically interconnected and act as both C&C servers and clients. Today, hackers adopt this approach to avoid detection and single-point failure.
In the P2P botnet approach, the infected devices scan for malicious websites or other devices. The bot carefully probes random IP addresses until it comes in contact with another infected machine. The bots then share updated commands or the latest versions of the malware.
Conclusion
Botnets are difficult to stop once they’ve taken root in users’ devices. To reduce phishing attacks and other issues, be sure you guard each of your devices against this malicious hijack.
GOW 27: Games of the Week
GOW 30: Games of the Week
Related post
0 comments
Leave a reply
Please Login or Register to Comment. Get StartedGOW 30: Games of the Week






