Hackers breach gamers, and user using pirated software: The Arts of stealing
On torrent sites, you will frequently discover that the identical consumer has uploaded many extraordinary games, applications, and key turbines that all have an equal size. The attackers declare to have to get admission to all of EA's services, telling clients inclined to pay $28 million for the stolen records that they will additionally reap "full functionality of exploiting on all ea services," as first stated by way of Motherboard.
In-game factors have been recognized to be used through cybercriminals for cash laundering purposes. "We are actively working with regulation enforcement officers and different specialists as a section of this ongoing crook investigation." They additionally shared screenshots of listing listings and supply codes as proof that the stolen facts are legitimate.
To distribute these spyware bundles, attackers will add them to torrent sites, create faux YouTube videos with hyperlinks to alleged license key generators, or create websites designed to simply promote spyware and adware bundles disguised as software programs cracks. According to the attackers, they should download supply codes for video games like FIFA 21 and the proprietary Frostbite recreation engine that’s the base of many high-profile games.

This has modified as software program installer monetization corporations have commenced to increasingly more group up with ransomware and password-stealing Trojan builders to distribute their malware.
It may additionally be tempting to strive to download the brand new video games or purposes for free, however doing so will sooner or later land you in a hotbed of the hassle as your pc turns into contaminated with adware, ransomware, and password-stealing Trojans.
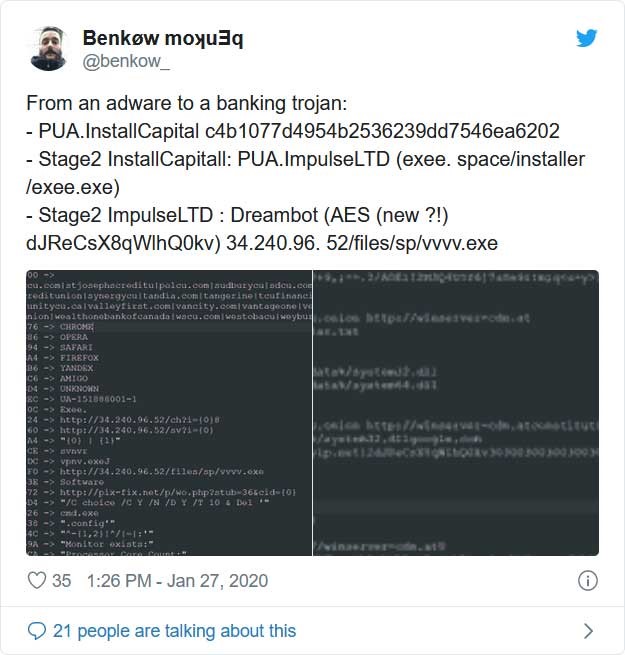
Security researcher Benkøw has these days seen that monetized installers pretending to be software program cracks and key mills are now often putting in password-stealing Trojans or faraway get entry to Trojans (RATs) when they are executed.
Tools that permit you to crack, or skip license restrictions, in copyrighted software programs have been around always and customers have constantly recognized that they face the threat of being contaminated with undesirable software programs via the use of them. YouTube additionally has its honest share of scammers who create movies promotion a sport cheat and then encompass a hyperlink to a file download. Like the torrent sites, these downloads are spyware and adware bundles that set up malware.






