BrakTooth, latest Bluetooth vulnerability with deadly capabilities
Recently, safety researchers from Singapore University of Technology and Design published a instead unsettling discovery related to the Bluetooth technology. They have observed a household of 20 protection flaws, which they jointly name ‘BrakTooth’.
The range of affected units is believed to be in billions. However, the have an impact on is distinct primarily based on the device’s underlying SoC board and Bluetooth software program stack.
The principal motive BrakTooth is the discuss of the city these days is due to the truth that it influences greater than 1,400 merchandise primarily based on thirteen distinct Bluetooth units bought via eleven of the world's main vendors. The have an impact on is huge.
What is BrakTooth succesful of?
BrakTooth can reportedly be exploited to behavior Denial-of-Service (DoS) assaults and allow arbitrary code execution on goal devices. The DoS assaults can disrupt the victim's Bluetooth connection or, in some cases, require Bluetooth connectivity to be restarted manually whilst arbitrary code execution can be used to erase consumer data, disable wi-fi connectivity, or have interaction with different devices.
What form of gadgets can fall sufferer to BrakTooth?
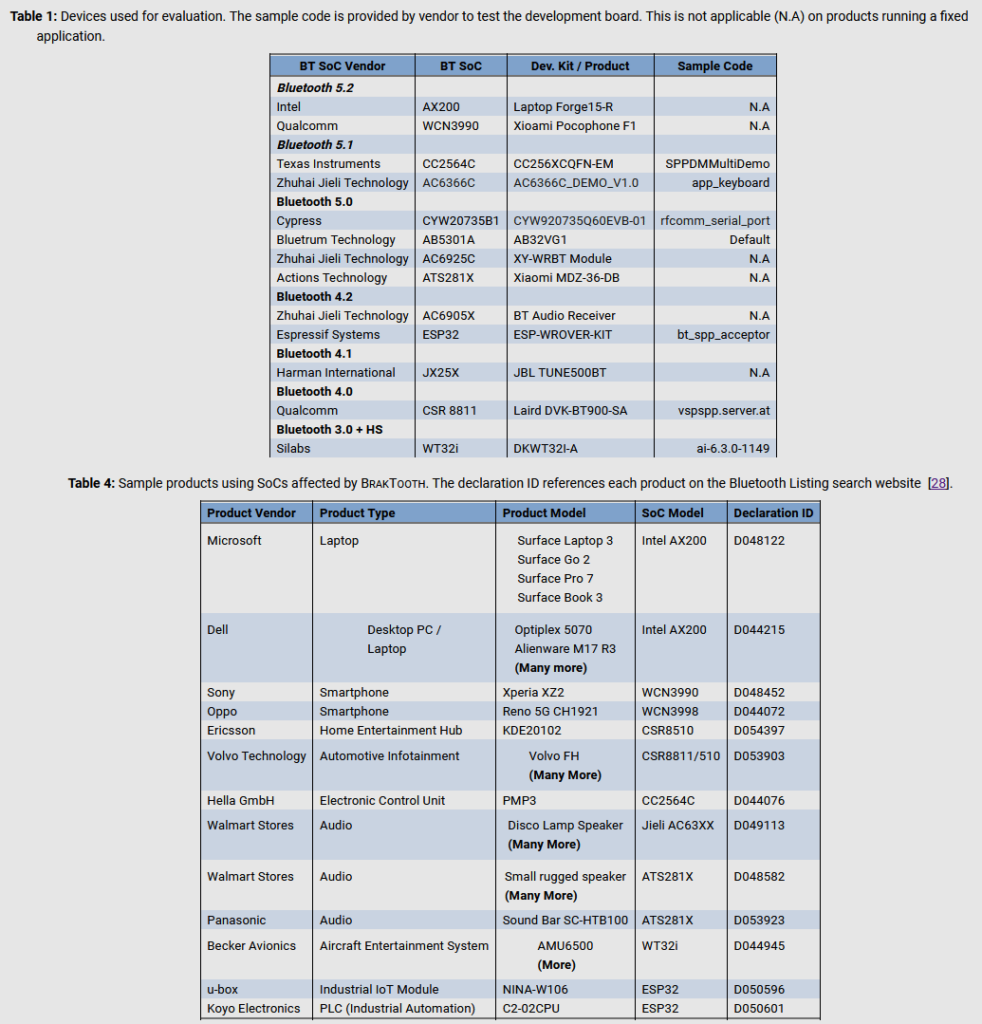
For their preliminary tests, the researchers solely examined the Bluetooth software program libraries for thirteen System-on-Chip (SoC) boards from eleven vendors.
However, subsequent lookup observed that the equal Bluetooth firmware used to be most probably used internal extra than 1,400 chipsets, used as the base for a huge assortment of devices.
These units may want to be:
• smartphones,
• laptops,
• keyboards,
• headphones,
• Industrial equipment,
• other Bluetooth-enabled devices.
Consequence of BrakTooth
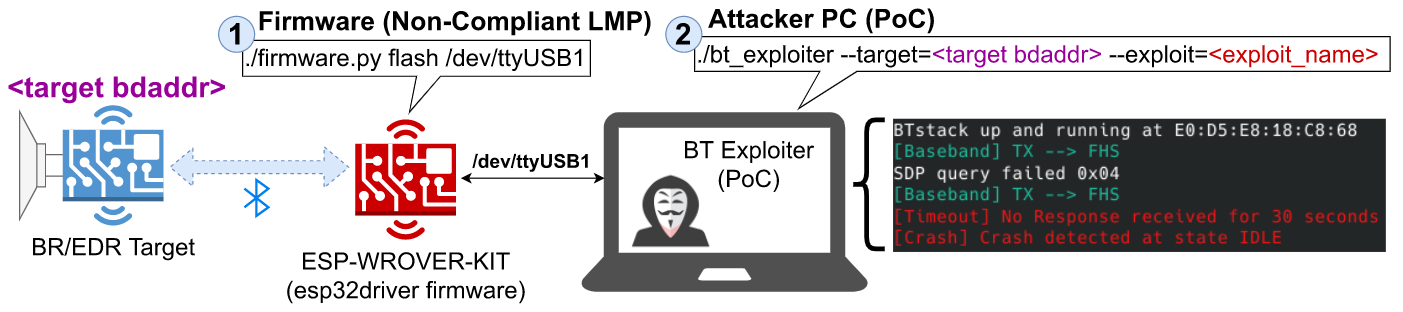
After investigating the vulnerability, the cybersecurity analysts have created various concrete assaults leveraging the BrakTooth vulnerabilities, that’s why they have cited the samples that typically launch the arbitrary code execution (ACE) or Denial of Service (DoS) on aimed devices.
• Arbitrary Code Execution in IoTs
• DoS in Laptops & Smartphones
• Freezing Audio Products
• Estimating the Scope of BrakTooth
• Product Design Considerations
Affected BT BR/EDR chipsets
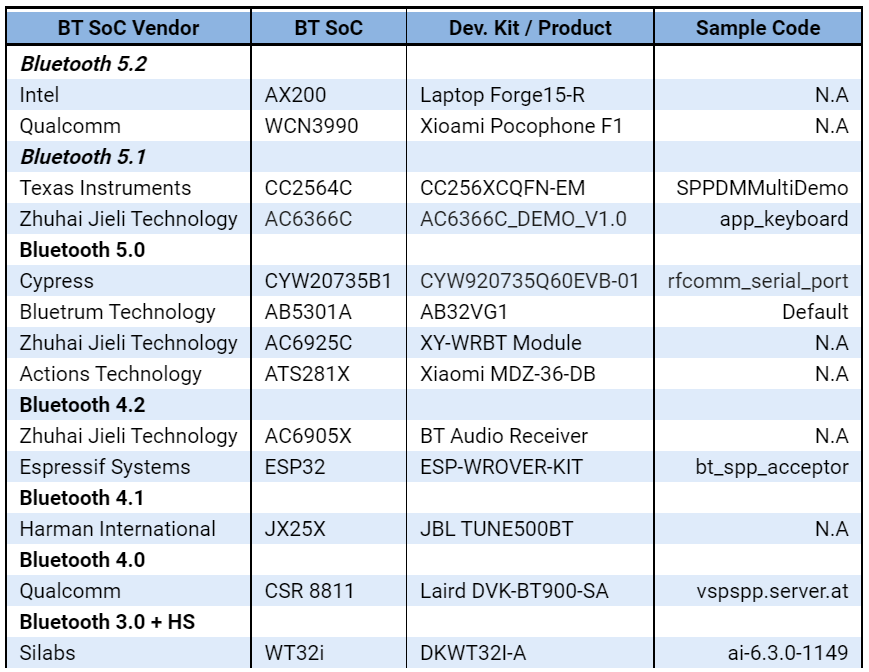
After going thru the detected vulnerability the professionals claimed that this vulnerability, is mutually acknowledged as BrakTooth, and it has affected SoCs from a wide variety of companies, that consist of the market veterans:-
• Intel
• Qualcomm
• Texas Instruments
• Infineon (Cypress)
• Silicon Labs
Types of units affected
Here is the listing of units that are affected stated below:-
• Smartphones
• Infotainment systems
• Laptop and computer systems
• Audio units (speakers, headphones)
• Home leisure systems
• Keyboards
• Toys
• Industrial tools like programmable common sense controllers (PLCs)
Vulnerabilities discovered
Here is the listing of vulnerabilities determined are stated below:-
• Feature Pages Execution (CVE-2021-28139)
• Truncated SCO Link Request (CVE-2021-34144)
• Duplicated IOCAP (CVE-2021-28136)
• Feature Response Flooding (CVE-2021-28135/28155/31717)
• LMP Auto Rate Overflow (CVE-2021-31609/31612)
• LMP 2-DH1 Overflow (Pending CVE)
• LMP DM1 Overflow (CVE-2021-34150)
• Truncated LMP Accepted (CVE-2021-31613)
• Invalid Setup Complete (CVE-2021-31611)
• Host Connection Flooding (CVE-2021-31785)
• Same Host Connection (CVE-2021-31786)
• LMP AU Rand Flooding (CVE-2021-31610/34149/34146/34143)
• LMP Invalid Max Slot Type (CVE-2021-34145)
• Max Slot Length Overflow (CVE-2021-34148)
• Invalid Timing Accuracy (CVE-2021-34147/Pending/Pending)
• Paging Scan Disable (Pending CVE)
BT Firmware Patches
Security Patch
After investigation, the protection analysts got here to be aware of that complete of eleven providers had been being attacked with the aid of this vulnerability. However, all the eleven companies have been requested months earlier than the protection researchers introduced their findings and knowledgeable about these safety issues. But after giving warnings for greater than ninety days there have been many providers who have no longer patched the vulnerability in time






