Play Store Banned 25 apps: Evina claims these apps could potentially Hack user credentials via Facebook
Google has deleted 25 apps from the Play Store for security reasons. These apps were accused of stealing users' Facebook data. This information was given to the company by French cybersecurity firm Evina. According to news from our partner website Zeebiz.com, some of these apps were related to steps counters, image editors, video editing apps, wallpaper apps, flashlights, file managers, and mobile games, which have been removed. If you have these apps on your phone too, then uninstall them immediately. More than half a million people have downloaded Super Wallpapers Flashlight and Padenatef from these apps. Some applications have been downloaded more than a million times. At the same time, the last three apps have been downloaded only 100 times. According to the researchers, these apps had a code that knew which app was running in the background. If Facebook is running in the background, then it will take all the information on Facebook. French cyber-security agency Evina reported the 25 malicious apps to Google. A faux login page was created by the apps on top of the actual Facebook login page to gain this data.
In the recent past, we have seen cybercriminals take advantage of serious situations like the COVID-19 pandemic to steal users' data. With the rate at which information spreads today, it doesn't take long for users to receive an email that reads, “the vaccine for Coronavirus is finally here. Click here to know more.” In a state of panic to know whether the cure is real, you click on the link and without realizing it, you are subject to a phishing, malware or ransomware attack. You can read more about phishing and cyber-attacks here. The apps offered a legitimate functionality, but they also contained malicious code. Evina researchers say the apps contained code that detected what app a user recently opened and had in the phone's foreground.
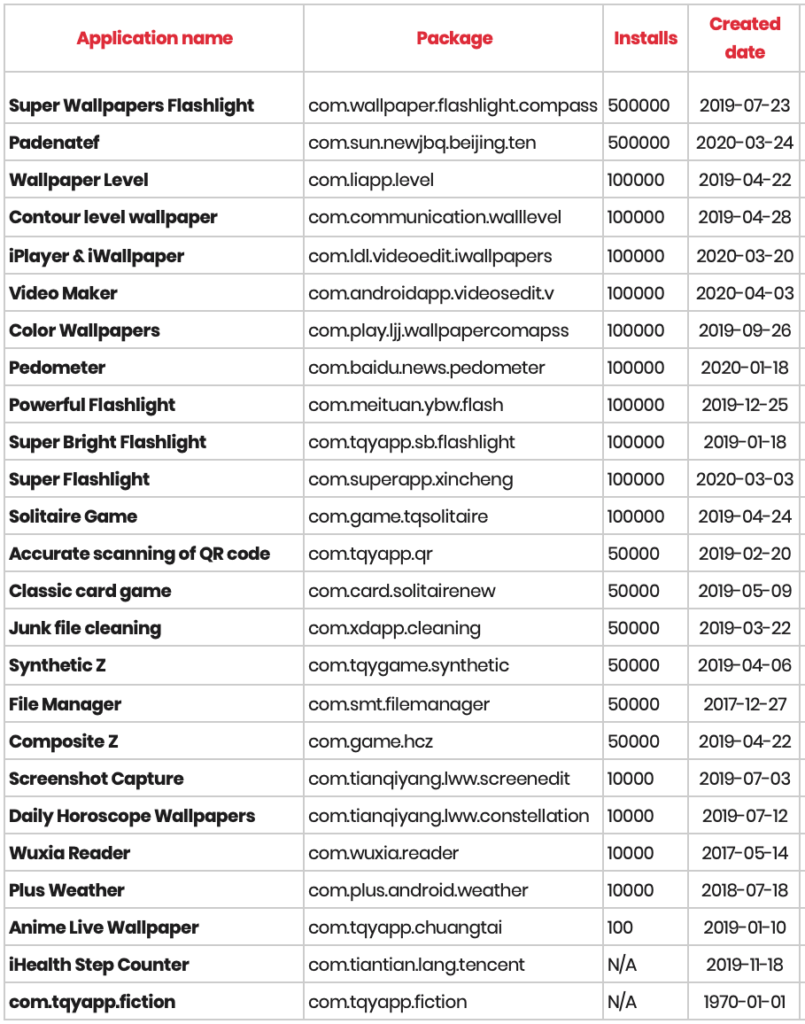
If the app was Facebook, the malicious app would overlay a web browser window on top of the official Facebook app and load a fake Facebook login page. According to XDADevelopers, “The malicious elements were disguised by legit functionality in these apps. Evina notes that these apps were masquerading as wallpaper apps, image and video editors, flashlight apps, games, and file managers on the Google Play Store.” To put things into perspective, these malicious apps were downloaded more than 2.4 million times.
If users entered credentials on this phishing page, the malicious app would log the data and send it to a remote server located at (the now-defunct) airshop.pw domain. Evina said it found the malicious code that stole Facebook credentials in 25 apps they reported to Google at the end of May. Google removed the apps earlier this month, after verifying the French security firm's findings. Some of the apps had been available on the Play Store for more than a year before they were removed.
How did these apps manage to get this sensitive information?
Why, users gave it up willingly, of course! These apps, despite appearing like ordinary games and wallpaper add-ons, open a browser window requiring a Facebook login. The user, if they’re not paying attention, may assume their Facebook account is required to use the app. But that login page isn’t real. Instead, it’s part of a phishing platform that harvests the data and saves it to a database of stolen records.
Actual attack?
These apps contained malicious code, which could detect the app opened in the background and foreground. If you open Facebook, the malicious app will show an overlaid web browser window on top of the Facebook app and load the fake login page. Thinking of it as a legit page, the owner will enter his/her credentials.






