Breification 14: Google’s AI creates its own inhuman encryption that reads emotion
The strategies advanced over time and in the end Bob and Alice had been in a position to talk in reality the usage of the shared key. Eve, on the different hand, had some good fortune decrypting the structures till Bob and Alice grew to be experts and then her capacity to crack the cipher failed. Bob and Alice, on the different hand, obtained clearly exact at sharing encrypted facts and many of their methods have been pretty unusual and unexpected, relying on calculations that weren’t frequent in “human generated” encryption.
A ciphertext might also even contain apparent metadata that identifies it as such. Therefore, it is no longer an intention for Eve to distinguish C from a random cost drawn from some distribution.
In this respect, Eve’s targets distinction from frequent ones for the adversaries of GANs. On the different hand, one should attempt to reformulate Eve’s aim in phrases of distinguishing the ciphertexts developed from two distinctive plaintexts.
Ultimately the researchers located that Bob and Alice have been true at devising a strong encryption protocol on their very own as lengthy as they valued security. Eve, on the different hand, had a heck of a time decrypting their communications. These skill robots will be capable to speak to every different in approaches that we – or different robots – won’t be capable to crack. I, for one, welcome our robotic cryptographic overlords.
Intuition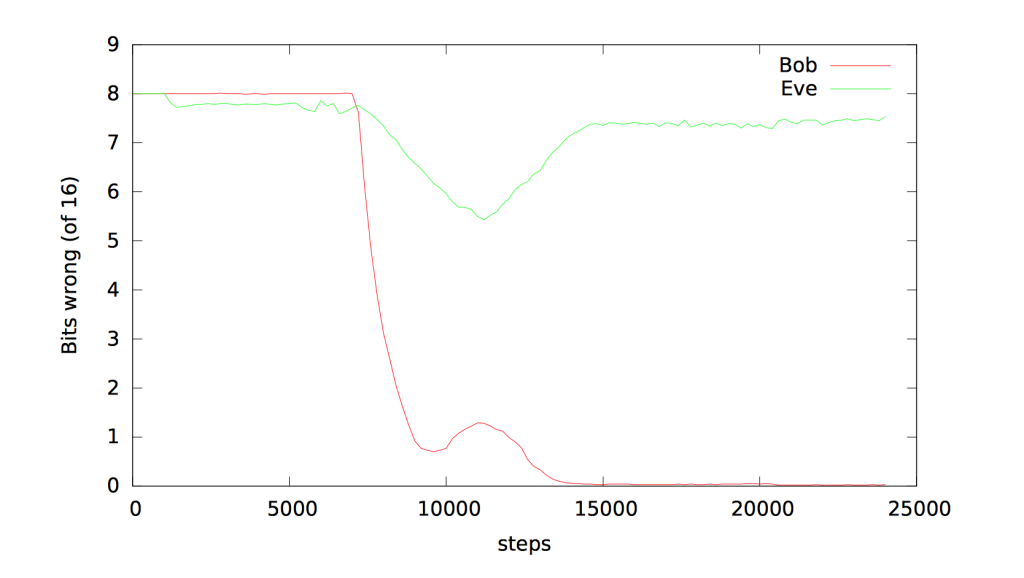
What takes place when you inform two clever computer systems to speak to every different in secret and undertake some other AI with breaking that conversation? You get one of the coolest experiments in cryptography I’ve considered in a while.
Bringing the advantages of AI to everyone
At Google AI, we’re conducting lookup that advances the ultra-modern in the field, making use of AI to merchandise and to new domains, and creating equipment to make sure that each person can get entry to AI.
AI in action
From our merchandise to our open-source platforms, we’re working to make sure that the advantages of AI are on hand to everyone.
Leading with research
Our lookup organizations are advancing the nation of the artwork in laptop science and making discoveries that empower billions of customers each and every day
Experiment description
The policies of the venture had been simple. Two neural networks, Bob and Alice, shared a secret key. Another neural network, Eve, used to be tasked with analyzing the communications between the two robots. There used to be one condition, a “loss function,” for every party. Eve and the recipient Bob’s plaintext had to be as shut to the unique plaintext as feasible whilst Alice’s loss feature relying on how a ways from random Eve’s guesses were. This created a generative adversarial community amongst the robots.
Conclusion
In short, Google Brain researchers have found that the AI, when top tasked, create oddly inhuman cryptographic schemes and that they’re higher at encrypting than decrypting. The paper, “Learning to shield communications with adversarial neural cryptography,” is reachable here.






